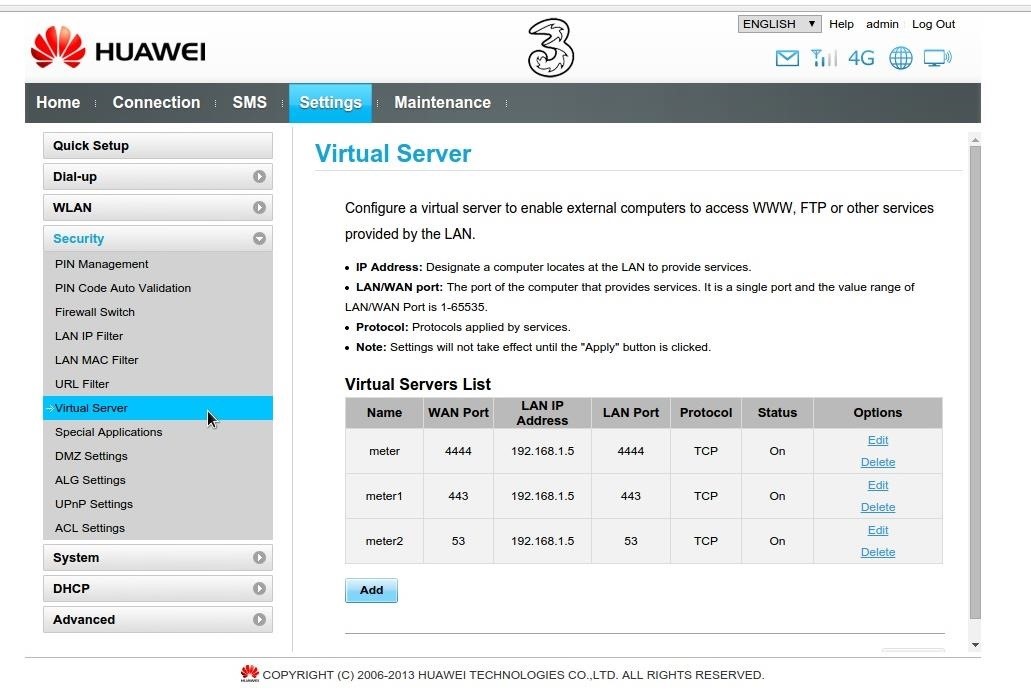
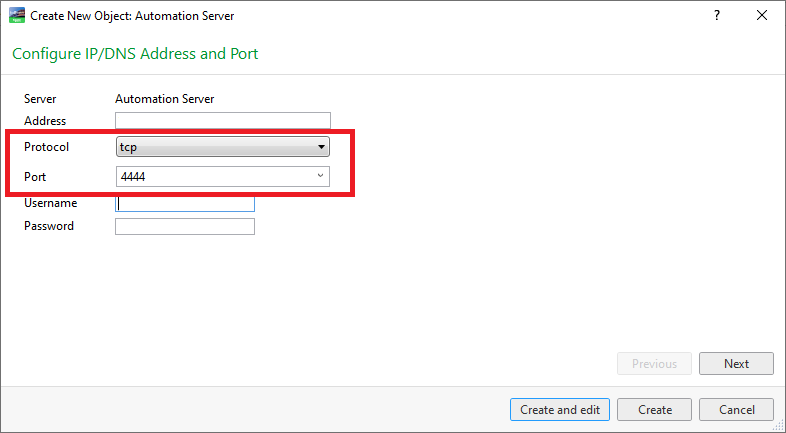
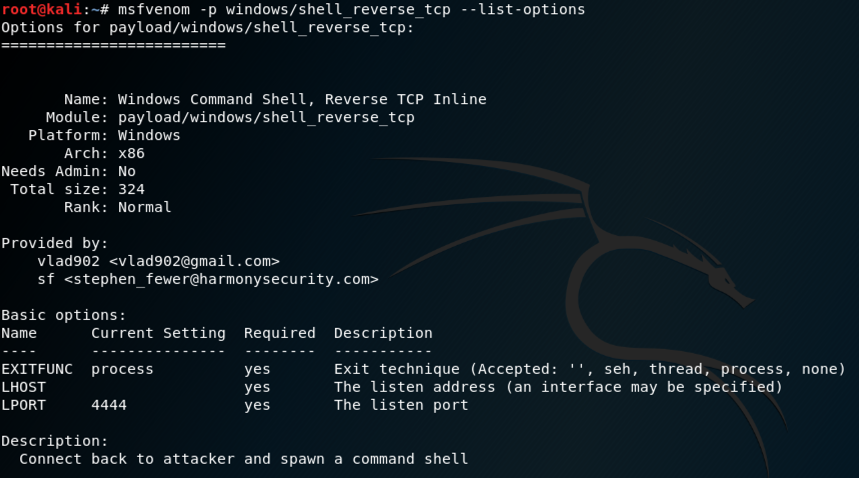
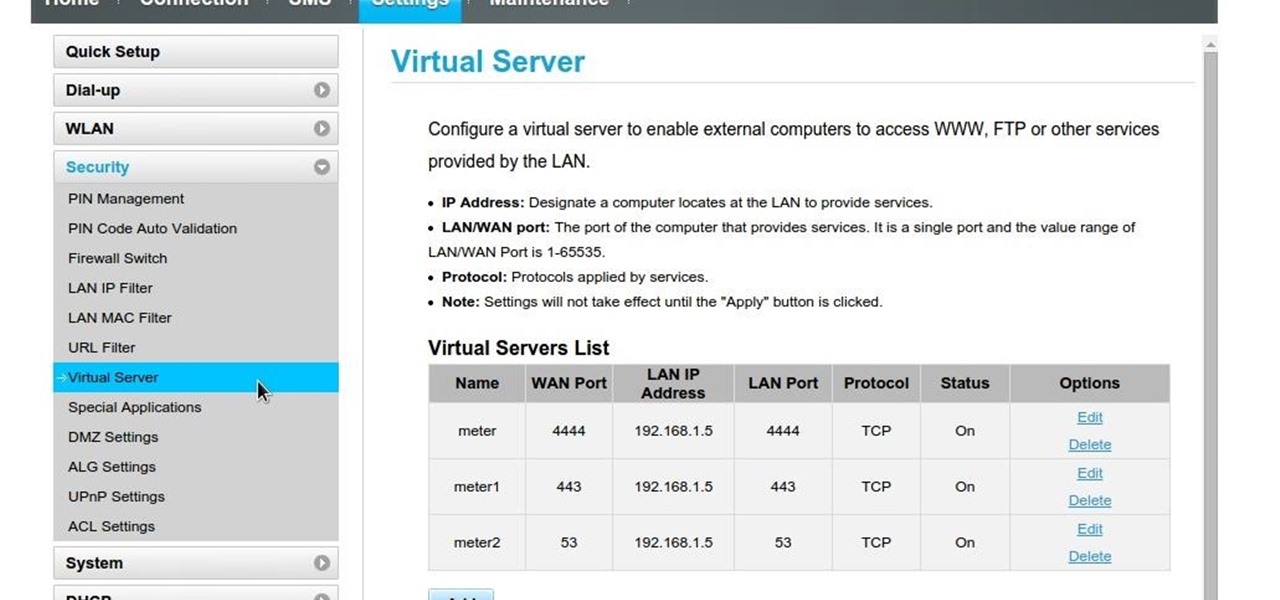
The hub cannot start because: "SEVERE: Port 4444 is busy, please choose a free port..." (the port is not in use) · Issue #742 · SeleniumHQ/docker-selenium · GitHub

networking - Port is locally opened but not detected by internet port checkers, something is wrong with port forwarding? - Super User

Deckboard defaults to port 4444 no matter what you enter · Issue #284 · rivafarabi/deckboard · GitHub
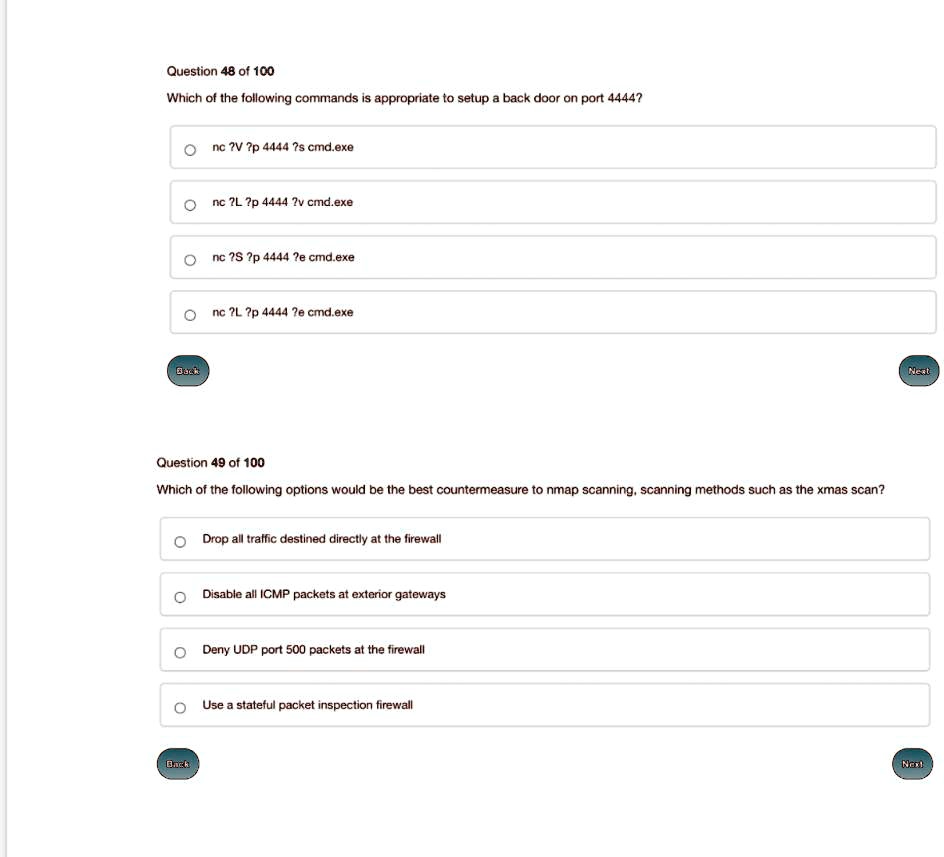
SOLVED: Question 48 of 100 Which of the following commands is appropriate to setup a back door on port 4444? nc ?V ?p 4444 ?s cmd.exe nc 7L?p 4444 2v cmd.exe nc?S?p4444?e








![Using the reverse Meterpreter on all ports - Mastering Metasploit - Third Edition [Book] Using the reverse Meterpreter on all ports - Mastering Metasploit - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788990615/files/assets/296c751d-68a4-4a63-8c41-83044874995a.png)